Pickle Rick - A TryHackMe Writeup
Once we start the machine we can do a normal nmap scan to see what ports we are working with.

Looks like we have an SSH server and a Webserver. Poking around the webserver it looks like a basic page asking for help, with no clickable links. However, if we view the page source we can see a Username in the comments.

If we continue poking around in the robots.txt file we see something that might possibly be a password. We can try using the username we found as well as this possible password to log into the SSH server.
No such luck. Let’s fire up gobuster to see if we can find any other hidden pages.
If we search by file extensions with know files such as php, we eventually find there is a login.php that we can try accessing.

Nice! Now lets try the username and possible password we found on this.
Perfect! We get a command panel

I’m not sure what kind of commands this panel will let us use, so lets try something basic like ls
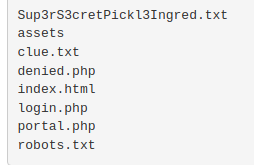
Boom! We have access to the server. Lets see what the files say with a cat command

Hmmm. So we can’t use cat, what other commands can we use to read files?
The more command is also blocked, but less appears to work!
And we have the first flag! There is also another file in the directory that gives us a clue to look around the file system for the other ingredient.
If we ls ../../../ our way through the system we can find there is another ingredient in rick’s home folder. We can read this with the less command again and we have our second ingredient.
We don’t have access to the root folder but if we use the sudo -l command we can see that we have wide open access with zero password, so we can just sudo ls /root to see what is in the root folder. And voila, we have the third ingredient. Just sudo less the file and we are done!
Last updated